How to Create OAuth Credentials for Sage Intacct REST
This guide will help you set up your Sage Intacct REST OAuth app to connect with Apideck. Sage Intacct is a cloud-based financial management and accounting software that provides comprehensive accounting solutions for businesses.
The Sage Intacct REST connector is currently auth-only. This means Apideck handles OAuth authentication and connection management, but you'll need to use the Apideck Proxy API to make API calls to Sage Intacct's REST endpoints. You'll receive the raw response from Sage Intacct's REST API.
💡 TIP: To understand the differences between Sage Intacct's SOAP/XML API (fully unified via Apideck Unify) and REST API (auth-only via Proxy), see our Sage Intacct API Guide.
Prerequisites
Before you begin, make sure you have the following:
- A Sage Intacct account with access to the Developer Portal
- An Intacct Web Services License Password
- An Apideck account
1. Enable the Sage Intacct REST connector in Apideck
First, enable the Sage Intacct REST connector in your Apideck dashboard:
- Go to your Apideck dashboard
- Navigate to Configuration > Accounting > Sage Intacct REST
- The connector will be available for configuration
2. Create OAuth App in Sage Developer Portal
Login to Sage Developer Console
- Go to the Sage Developer Console
- Sign in with your Sage account credentials
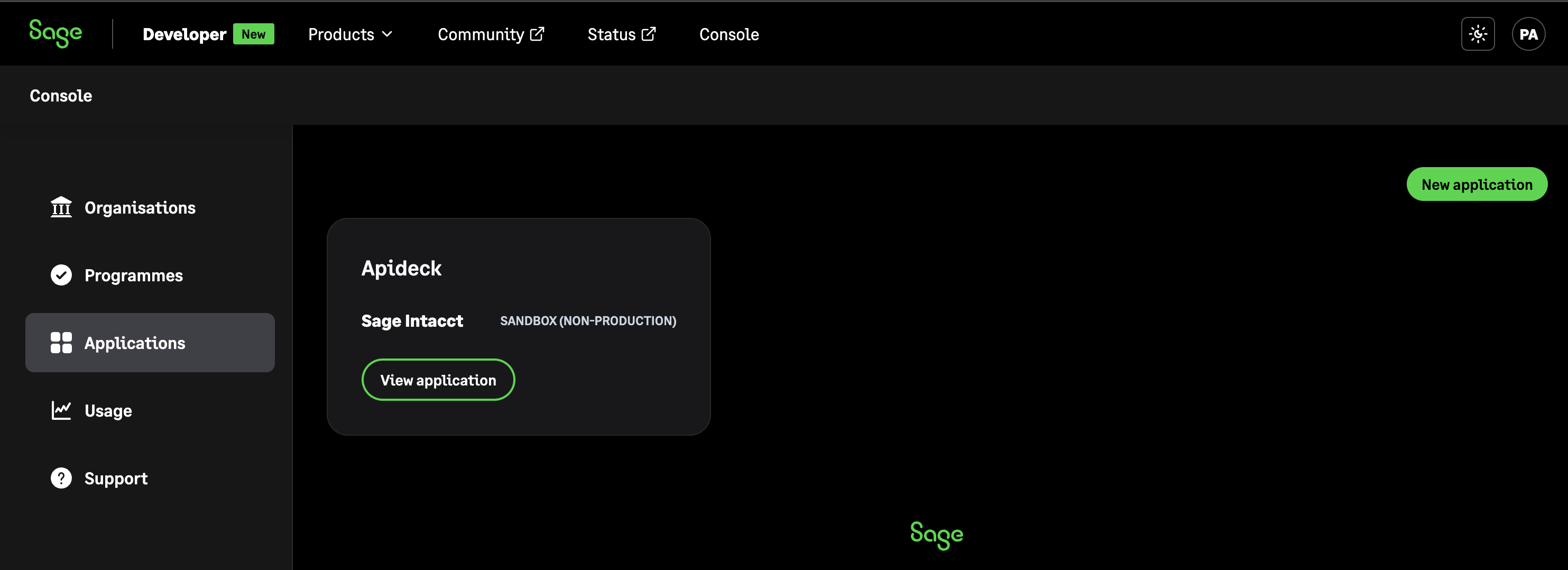
Navigate to Applications
- Click on Applications in the navigation menu
- You'll see a list of your existing applications (if any)
Create New Application
- Click Create new application to start setting up your OAuth app
Select API Type
- Select API - REST as the API type for your application
- This ensures your app uses the REST API endpoints
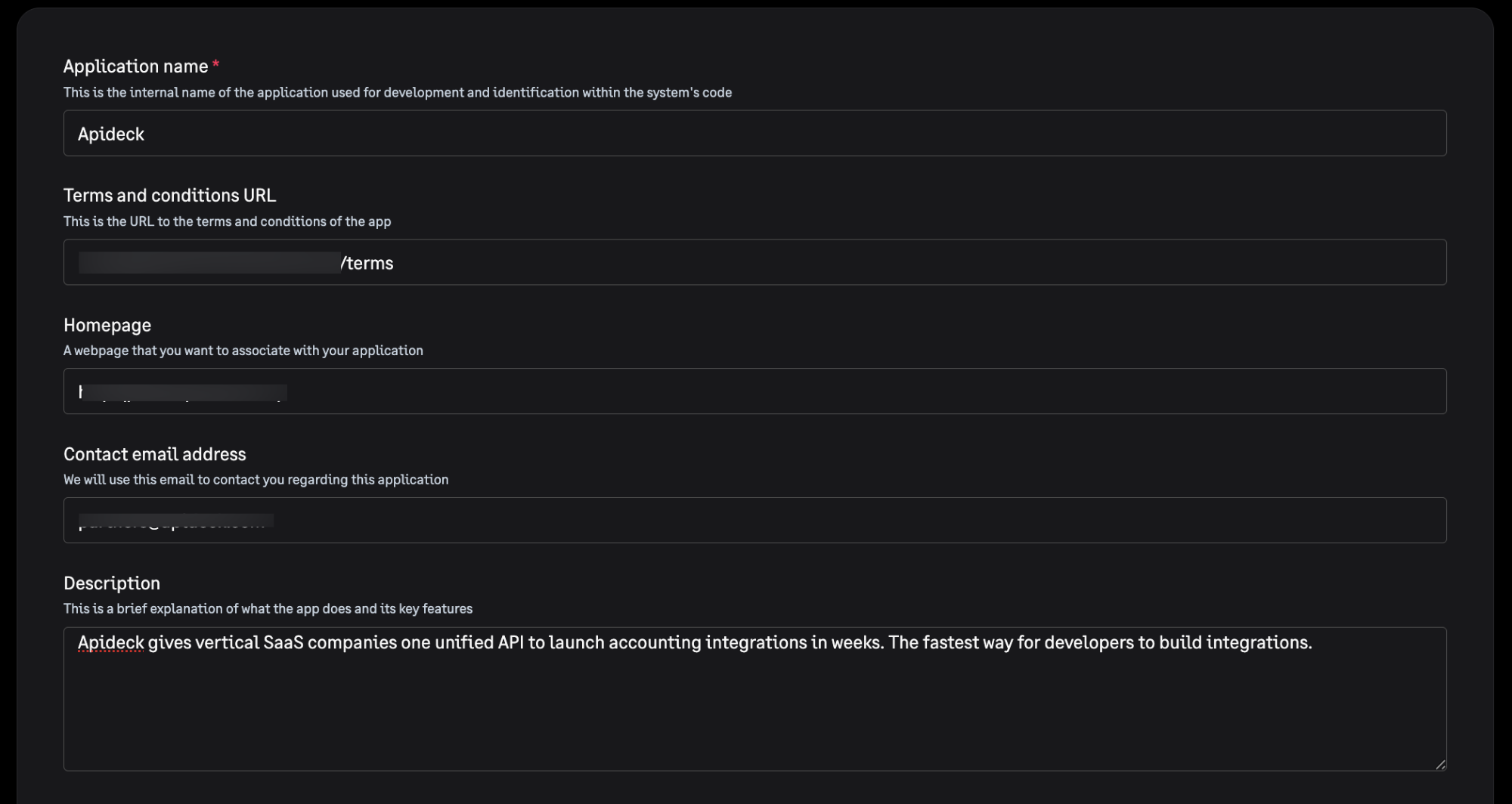
Configure Application Details
Fill out the basic information for your app:
- Name: Enter a descriptive name for your application (e.g., "Apideck Integration")
- Terms and conditions URL: Provide a URL to your terms and conditions (optional)
- Homepage: Enter your application's homepage URL
- Contact email address: Provide an email address for support inquiries
- Description: Provide a brief description of your integration
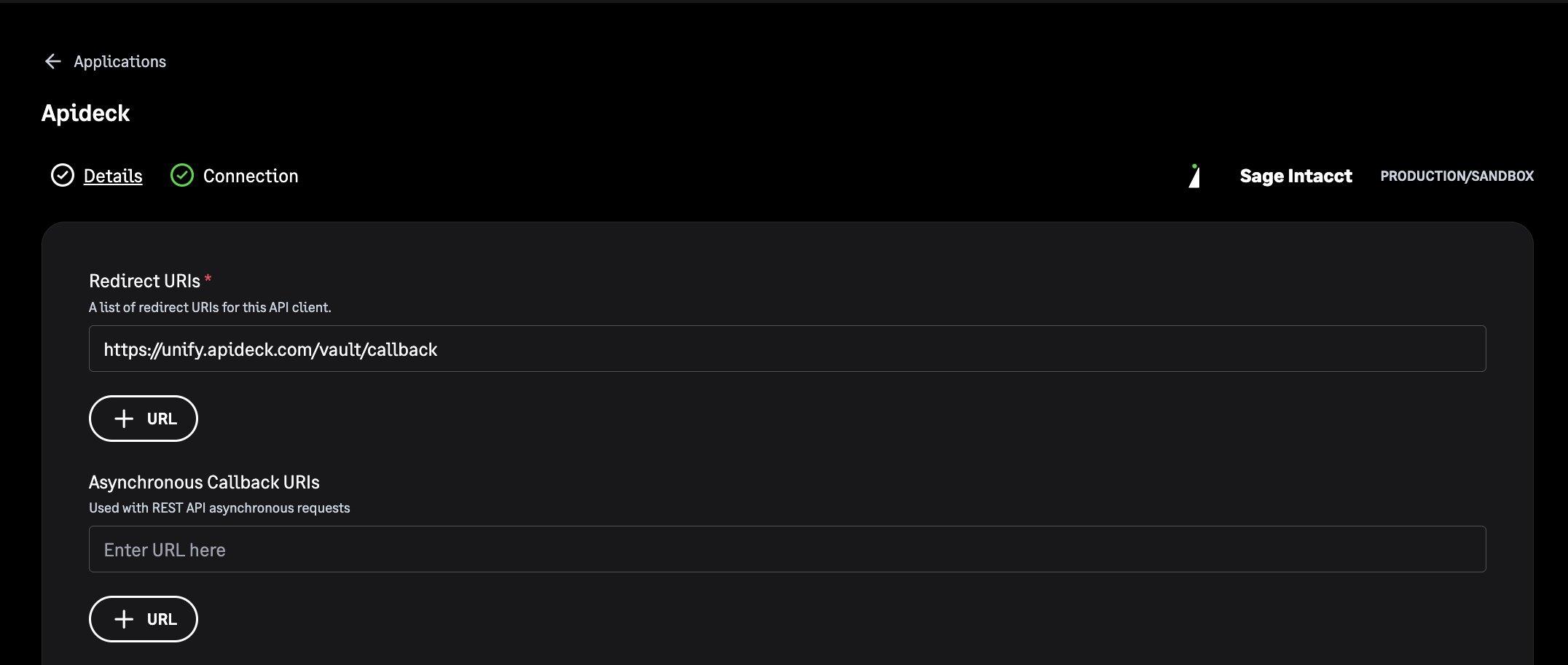
Configure Redirect URI
- Go to the next step in the application creation process
- Add the following redirect URI:
https://unify.apideck.com/vault/callback
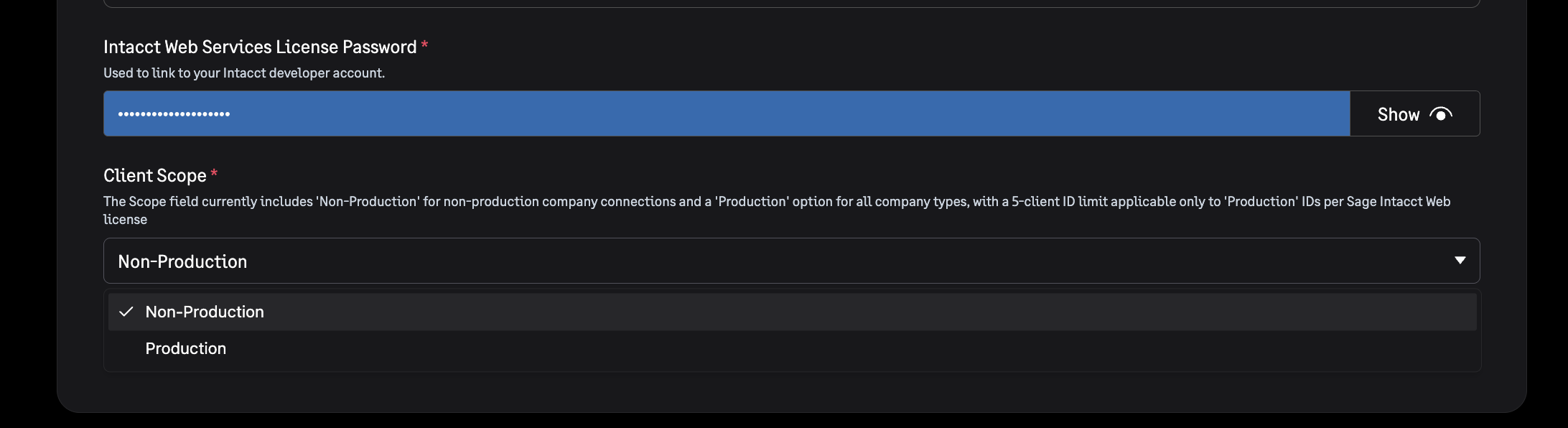
Add Intacct Web Services License Password
- Enter your Intacct Web Services License Password
- This password is required for authentication with Sage Intacct
Select Client Scope
- Choose the appropriate Client Scope for your application:
- Production: For live/production environments
- Non-production: For testing and development environments
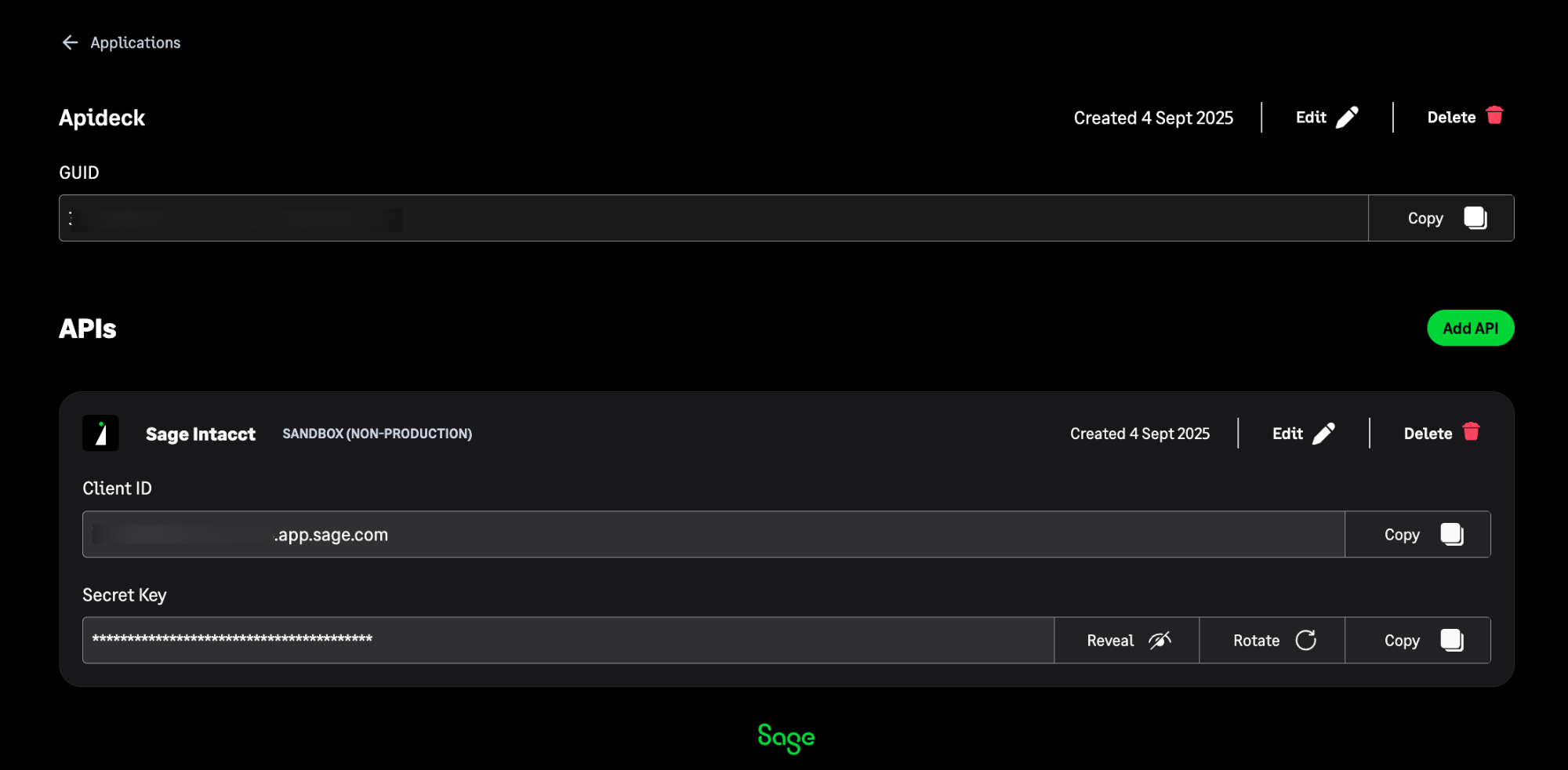
Copy OAuth Credentials
After creating your application, you'll see your OAuth credentials:
- Client ID
- Secret Key
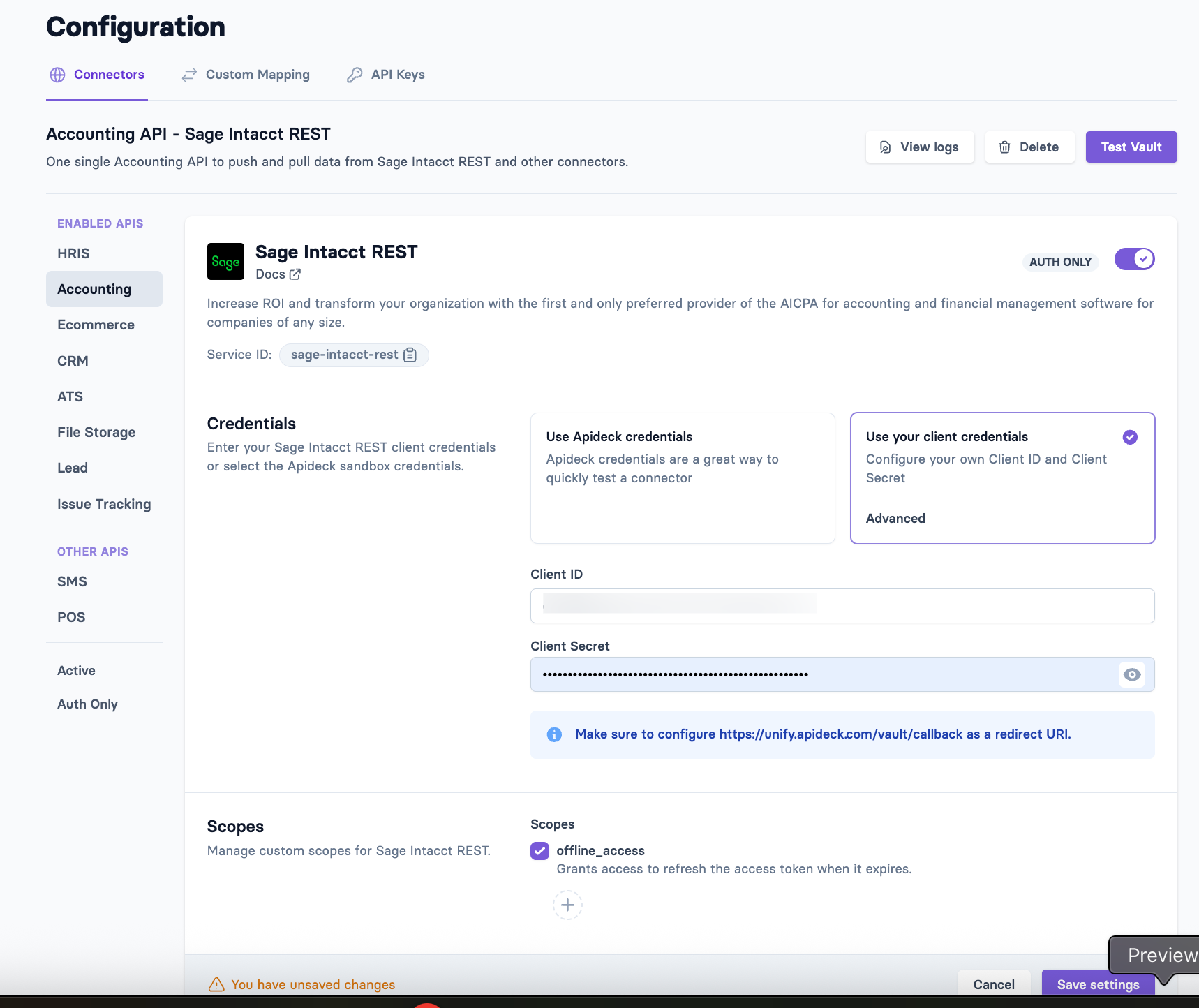
3. Configure connector in Apideck
Now that you've successfully created your Sage Intacct REST OAuth app, you can add the credentials in the Apideck dashboard.
Add Credentials
- Go to your Apideck dashboard
- Navigate to Configuration > Accounting > Sage Intacct REST
- Enter the following credentials:
- Client ID: Paste the Client ID you copied from the Sage Developer Portal
- Client Secret: Paste the Client Secret you copied from the Sage Developer Portal
- Click Save settings to save your credentials
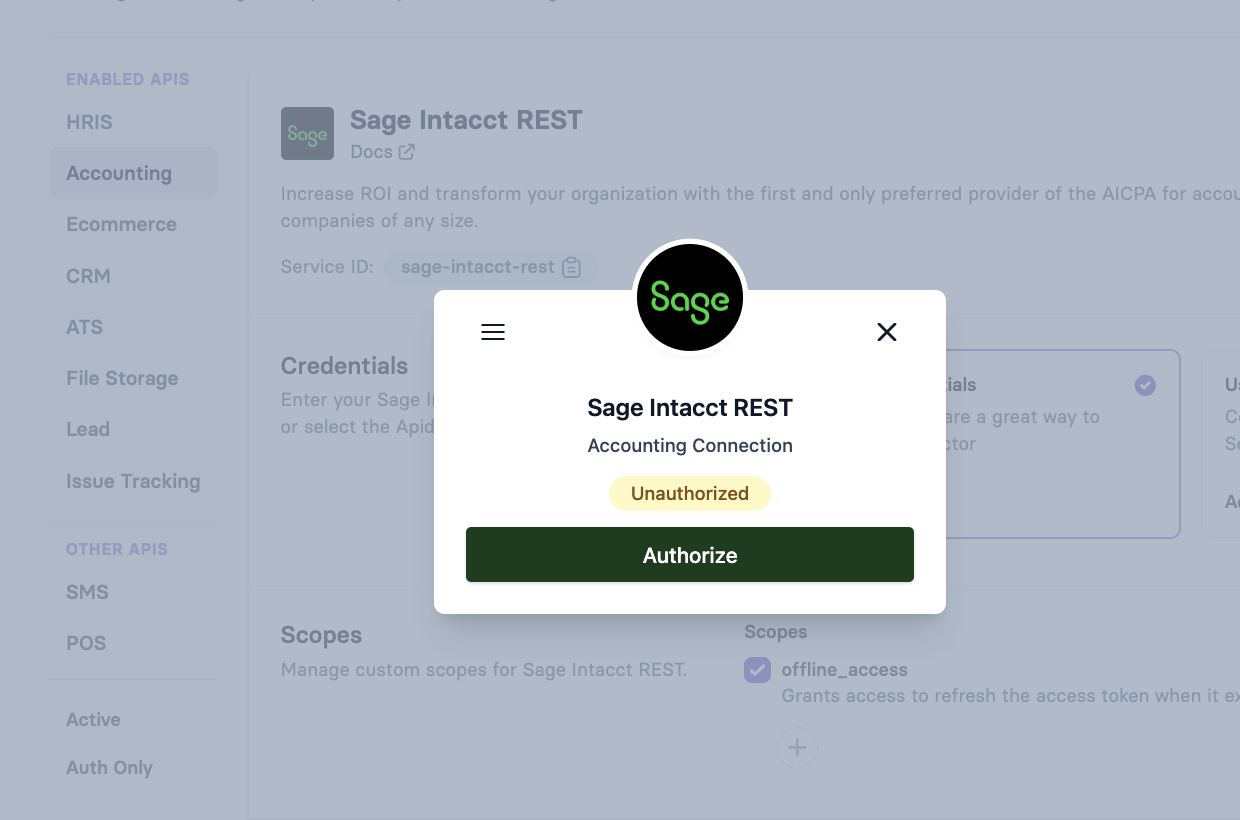
4. Test the Connection
You can test your Sage Intacct REST connector by clicking Test Vault in the connector configuration page.
Authorize the Connection
- Click Authorize
Login with Sage Intacct Credentials
- Log in with your Sage Intacct user credentials
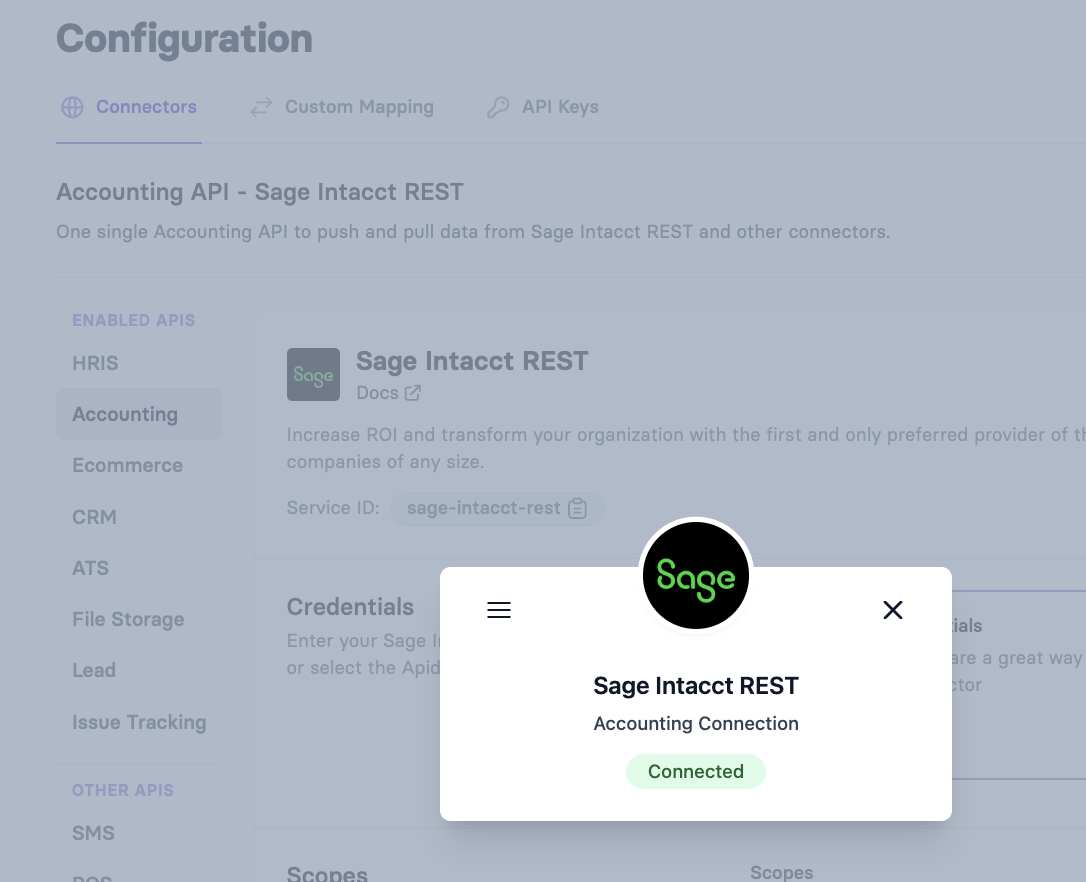
Verify Connection Status
- After successful authorization, your connection should show as Connected
Do your first API call to the Sage Intacct REST API
Since the Sage Intacct REST connector is auth-only, you'll use the Apideck Proxy API to make calls to Sage Intacct's REST endpoints.
- Connect through Vault
- Test with this call to the Proxy API:
Replace {APIDECK_APP_ID} and {APIDECK_API_KEY} with your actual Apideck credentials. Replace the x-apideck-downstream-url with the appropriate Sage Intacct REST API endpoint according to Sage Intacct's REST API documentation.