How to Create OAuth Credentials for GitLab
This guide will help you set up your GitLab OAuth app to connect with Apideck. GitLab is a complete DevOps platform that enables you to manage projects, issues, groups, and other resources through the GitLab API.
To create a connection with GitLab, you need to complete the following steps:
- Enable the GitLab connector in Apideck
- Create OAuth application in GitLab
- Find your Group ID
- Configure connector in Apideck
- Test the connection
Prerequisites
Before you begin, make sure you have the following:
- A GitLab.com account - You can sign up here
- An Apideck account
- Access to a GitLab group (you'll need the Group ID for configuration)
1. Enable the GitLab connector in Apideck
First, enable the GitLab connector in your Apideck dashboard:
- Go to your Apideck dashboard
- Navigate to Configuration > Issue Tracking > GitLab
- The connector will be available for configuration
2. Create OAuth application in GitLab
Login to GitLab
- Go to GitLab.com
- Sign in with your GitLab account credentials
Navigate to Applications
- After logging in, click your profile picture at the top right corner of the page
- Select "Preferences" from the dropdown menu
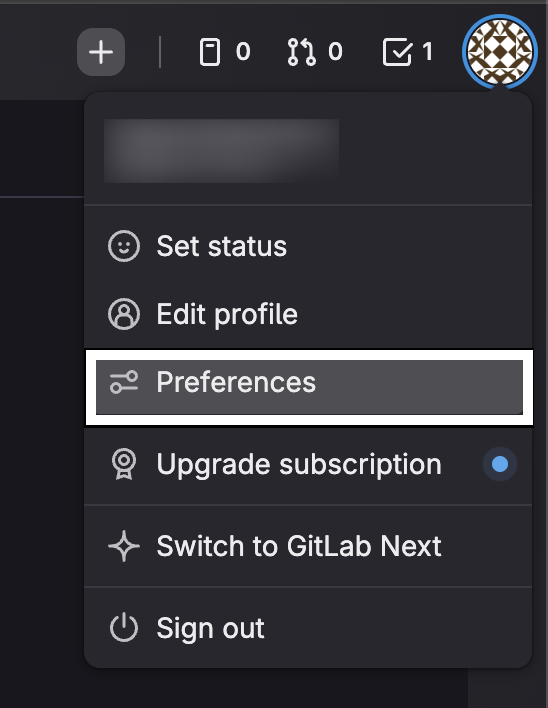
- In the left sidebar, scroll down and click on "Applications"
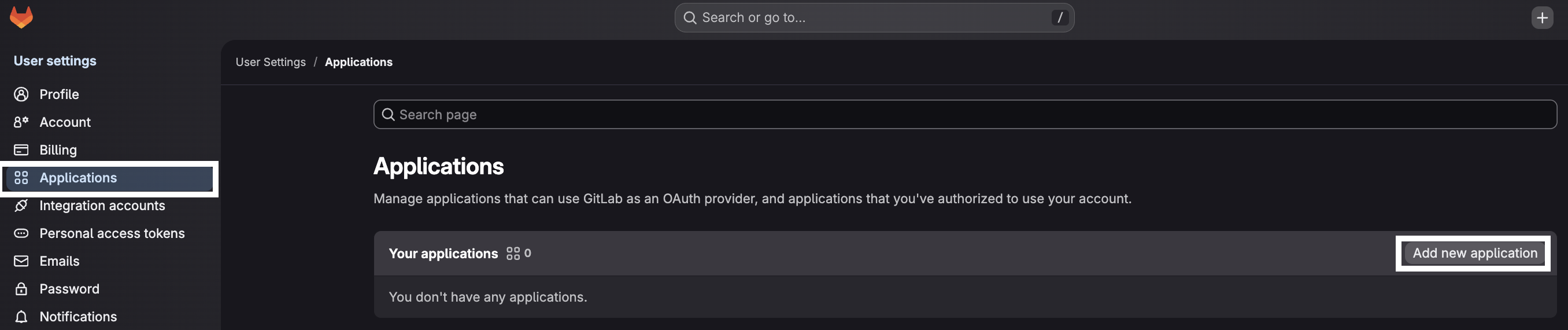
Configure Application Details
Fill out the application information:
- Name: Enter a meaningful name for your application (e.g., "Apideck Integration")
- Redirect URI: Enter
https://unify.apideck.com/vault/callback - Scopes: Select the scopes you need. For full API access, select:
api- Access the authenticated user's APIread_user- Read the authenticated user's personal informationread_api- Read-only access to the API
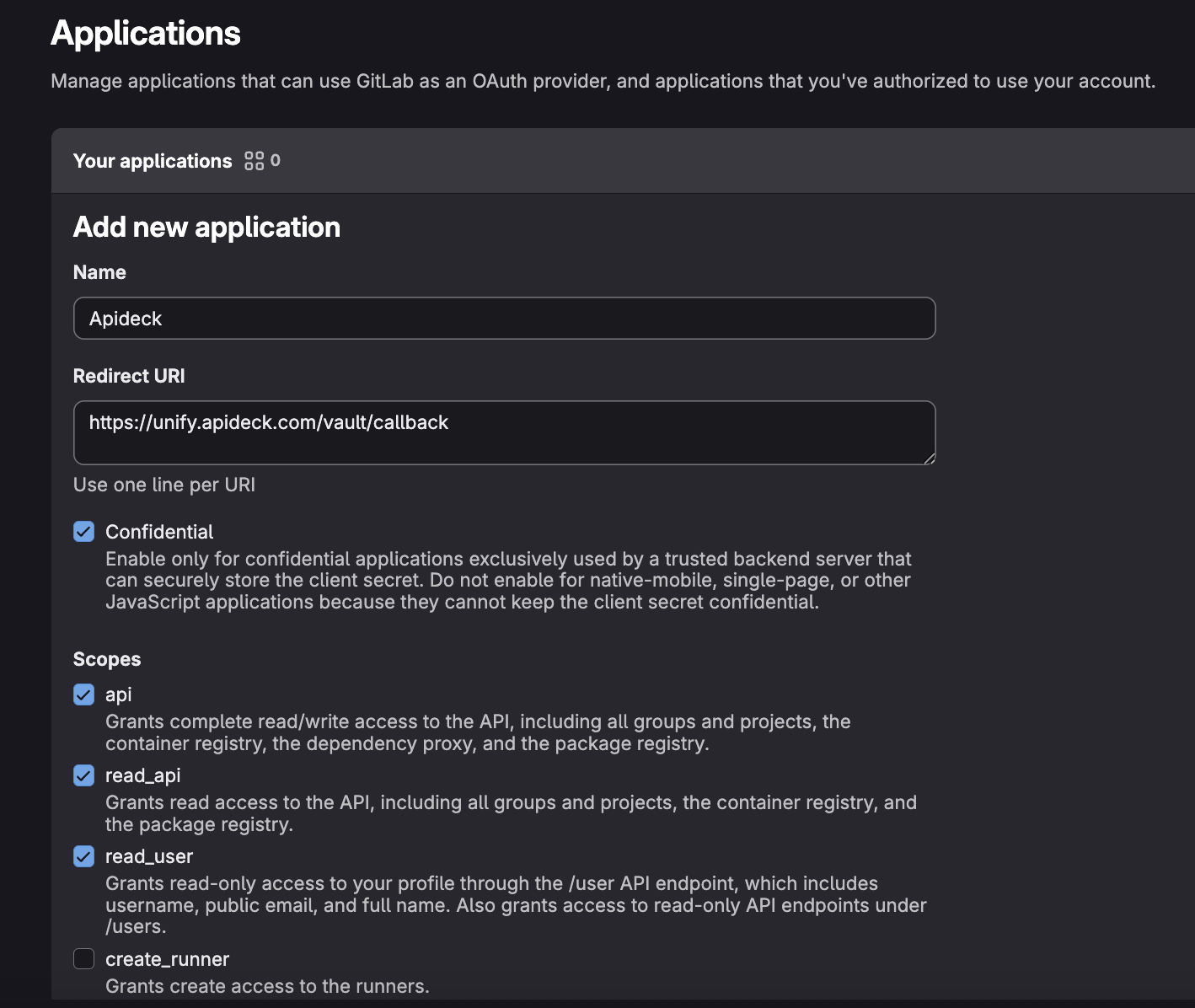
- Click "Save application" to create the OAuth application
Copy OAuth Credentials
After creating your application, GitLab will display the following credentials:
- Application ID (Client ID) - This is your OAuth Client ID
- Secret (Client Secret) - This is your OAuth Client Secret
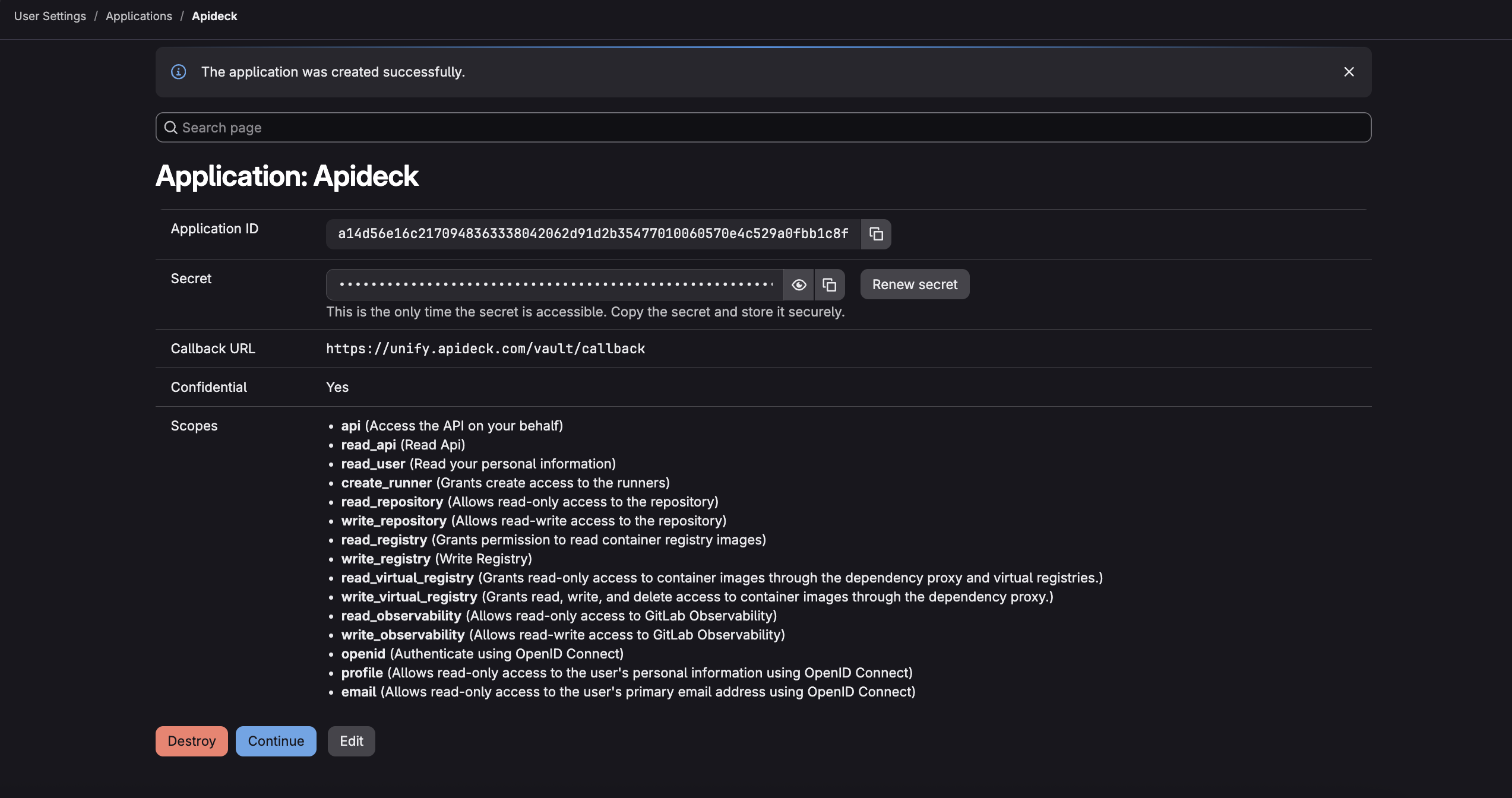
💡 TIP: Copy the "Application ID" and "Secret". The secret will only be shown once and cannot be retrieved later.
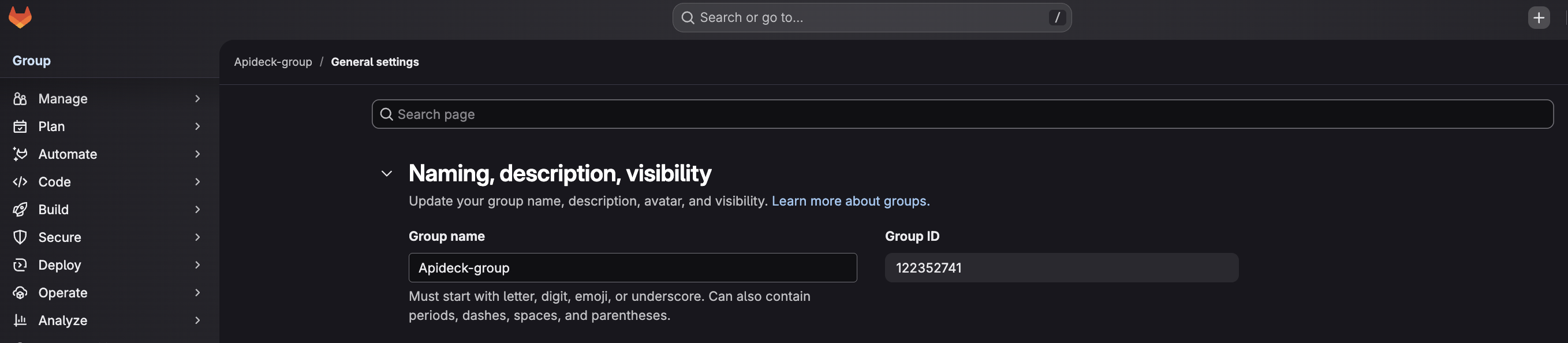
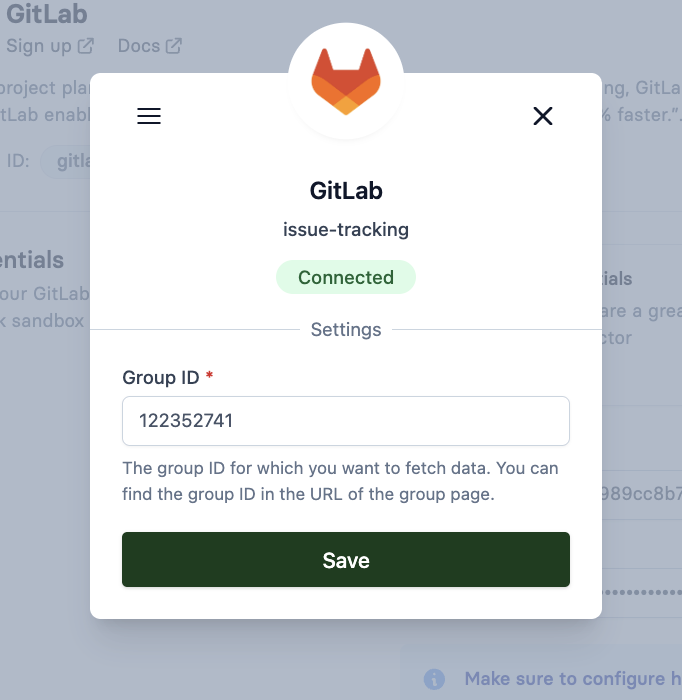
3. Find your Group ID
You'll need to provide a Group ID when configuring the connector. The Group ID can be either a numeric identifier or the group's path/name. GitLab accepts both formats.
Method 1: From the Group Page (Recommended)
- Navigate to your GitLab group by clicking on it from the dashboard or groups list
- Look at the URL in your browser's address bar
- The Group ID may appear in the URL, or you can find it by:
- Clicking the Actions menu (three dots or ellipsis icon) in the upper-right corner of the group page
- Selecting "Copy Group ID" if available in your GitLab version
Method 2: From the Group URL
You can find the group identifier directly in the URL:
- If you see a URL like:
https://gitlab.com/groups/my-group-name- you can usemy-group-nameas the Group ID - Or:
https://gitlab.com/-/g/123(where123is the numeric Group ID) - you can use123as the Group ID
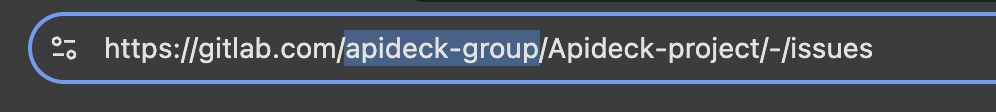
💡 TIP: GitLab accepts both the numeric ID (e.g., 122352741) and the group path/name (e.g., Apideck-group) as valid Group ID values.
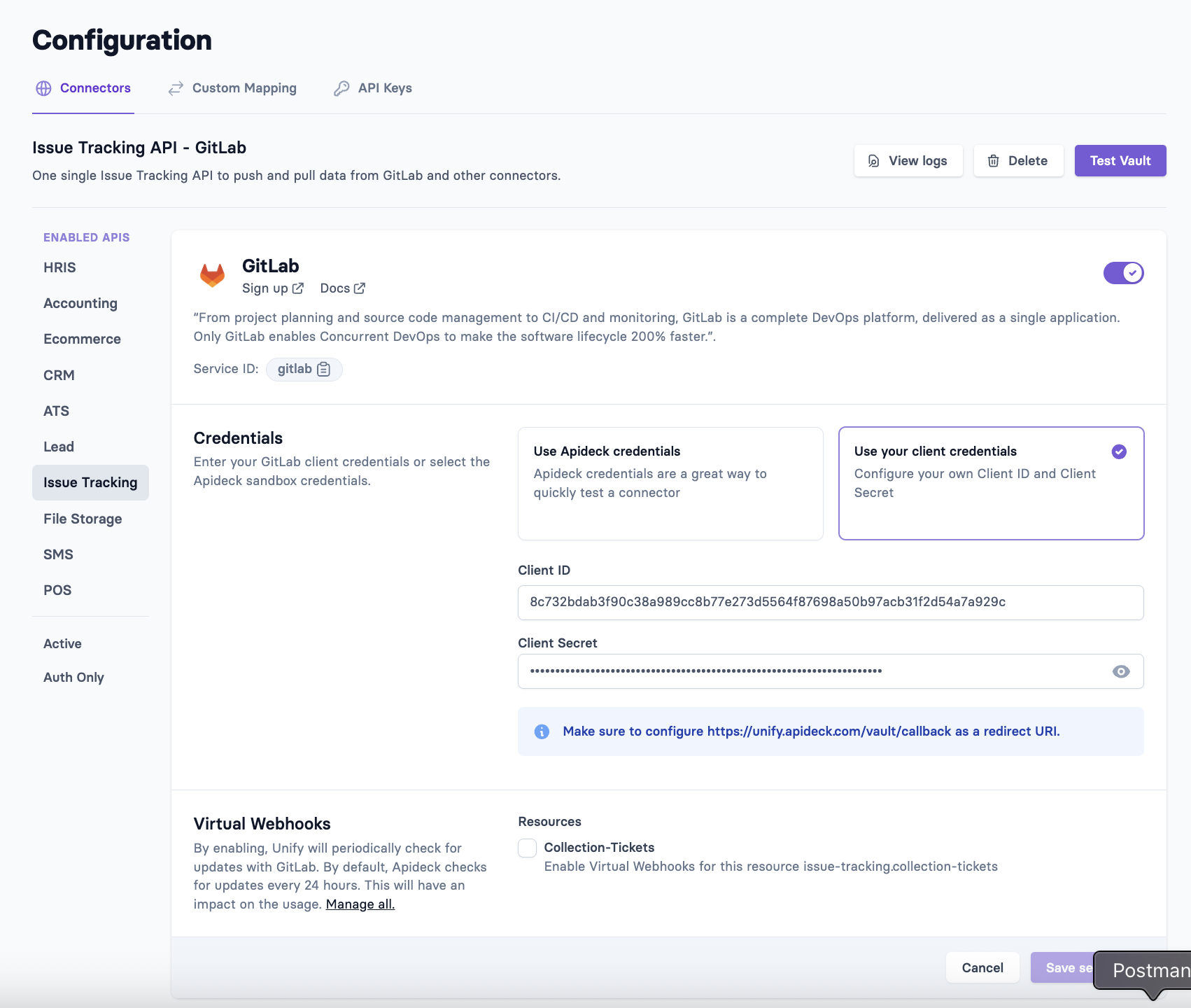
4. Configure connector in Apideck
Now that you've successfully created your GitLab OAuth app and found your Group ID, you can add the credentials in the Apideck connector configuration.
Add OAuth Credentials
- Go to your Apideck dashboard at https://platform.apideck.com/
- Navigate to Configuration > Issue Tracking > GitLab
- Select "Use your GitLab client credentials" and enter:
- Client ID: Paste the Application ID you copied from GitLab
- Client Secret: Paste the Secret you copied from GitLab
5. Test the connection
You can test your GitLab connector by clicking Test Vault in the Apideck dashboard.
- Click Test Vault to trigger the OAuth flow
- Click Authorize to grant access to your GitLab account
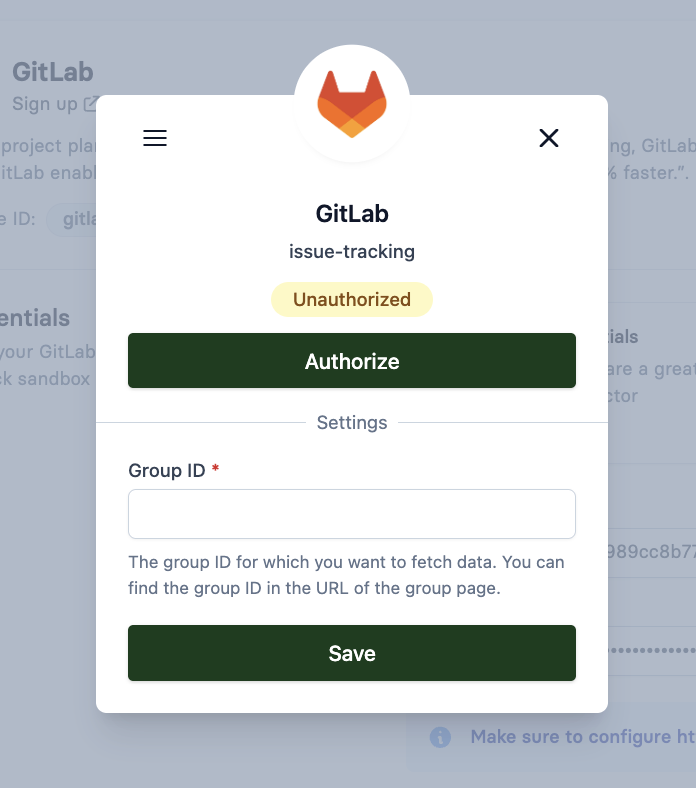
- Enter your Group ID or group name (can be numeric like
122352741or the group path/name likeApideck-group) - Click Save to save your configuration
- Your integration will now show as Connected
Do your first API call to the Issue Tracking API
Test with this call:
Your GitLab OAuth credentials are now configured and ready to use! 🎉
Troubleshooting
Error: Invalid redirect_uri
If you receive an error about an invalid redirect URI, ensure that:
- The redirect URI is exactly
https://unify.apideck.com/vault/callback(case-sensitive) - The redirect URI has been properly added to your application in GitLab's Applications settings
Error: Group Not Found
If you receive an error about the group:
- Verify that the Group ID is correct (can be numeric like
122352741or the group path/name likeApideck-group) - Ensure you have access permissions to the specified group
- Check that the group exists and is accessible with your user account
- If using a group path/name, ensure it matches exactly (case-sensitive)
Error: Insufficient scopes
If you're receiving permission errors, ensure that you've selected all the necessary scopes in your GitLab OAuth application:
api- Required for full API accessread_user- Required for user informationread_api- Required for read-only API access
You may need to reauthorize the application with additional scopes.