How to register an OAuth app for Microsoft Entra (Azure Active Directory)
Microsoft Entry (Azure Active Directory) is a cloud-based identity and access management service, which can be used to manage employees.
Register your app with Azure
1. Create a new app
Go to the Azure App registration page and click the New registration button

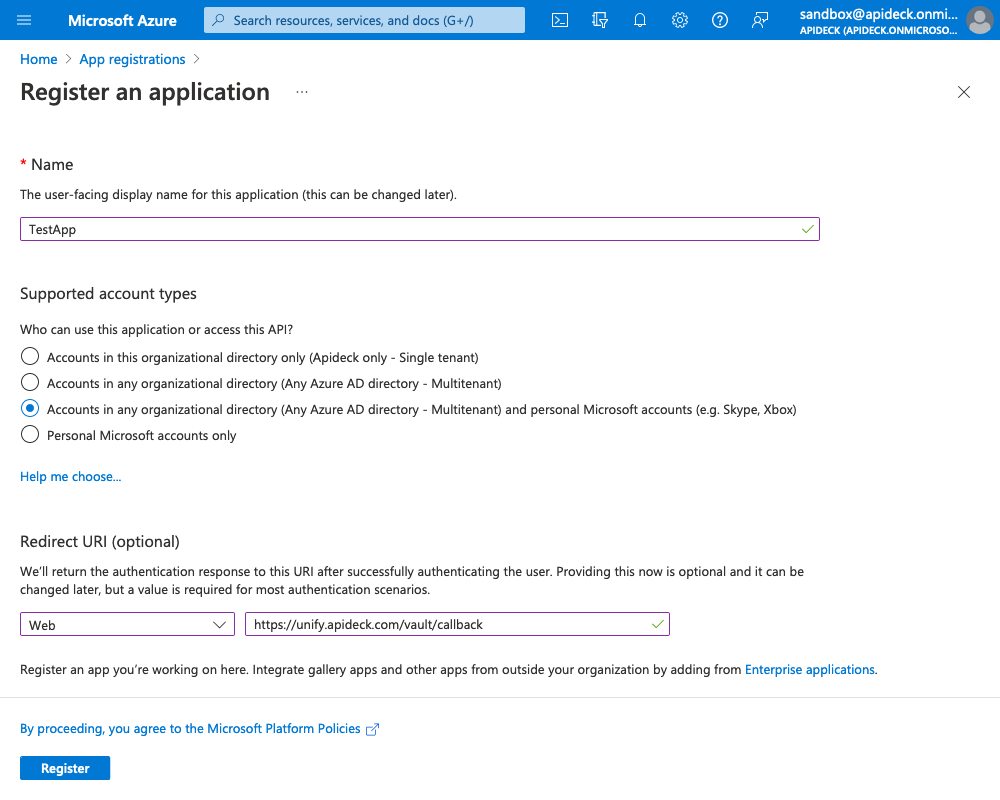
2. Enter app details
On the next page, enter your application's registration information:
- Name - Enter a meaningful application name that will be displayed to your users. Most of the time this should be your company's name.
- Supported account types - Select Accounts in any organizational directory and personal Microsoft accounts
- You can select other options if they are more relevant for you. This option supports the broadest user base.
- Redirect URI - Set the platform to
Weband usehttps://unify.apideck.com/vault/callbackas the redirect URI. This is the default redirect URI for Apideck.
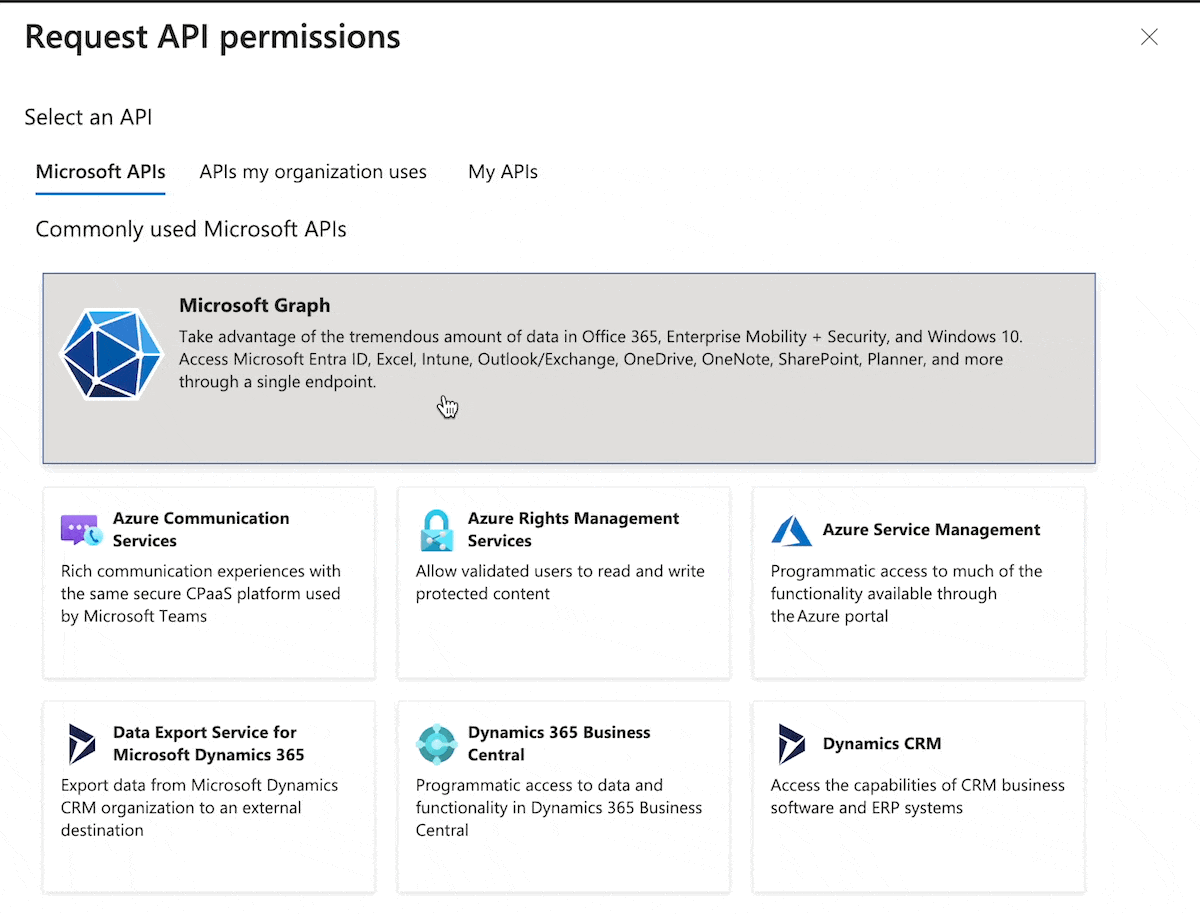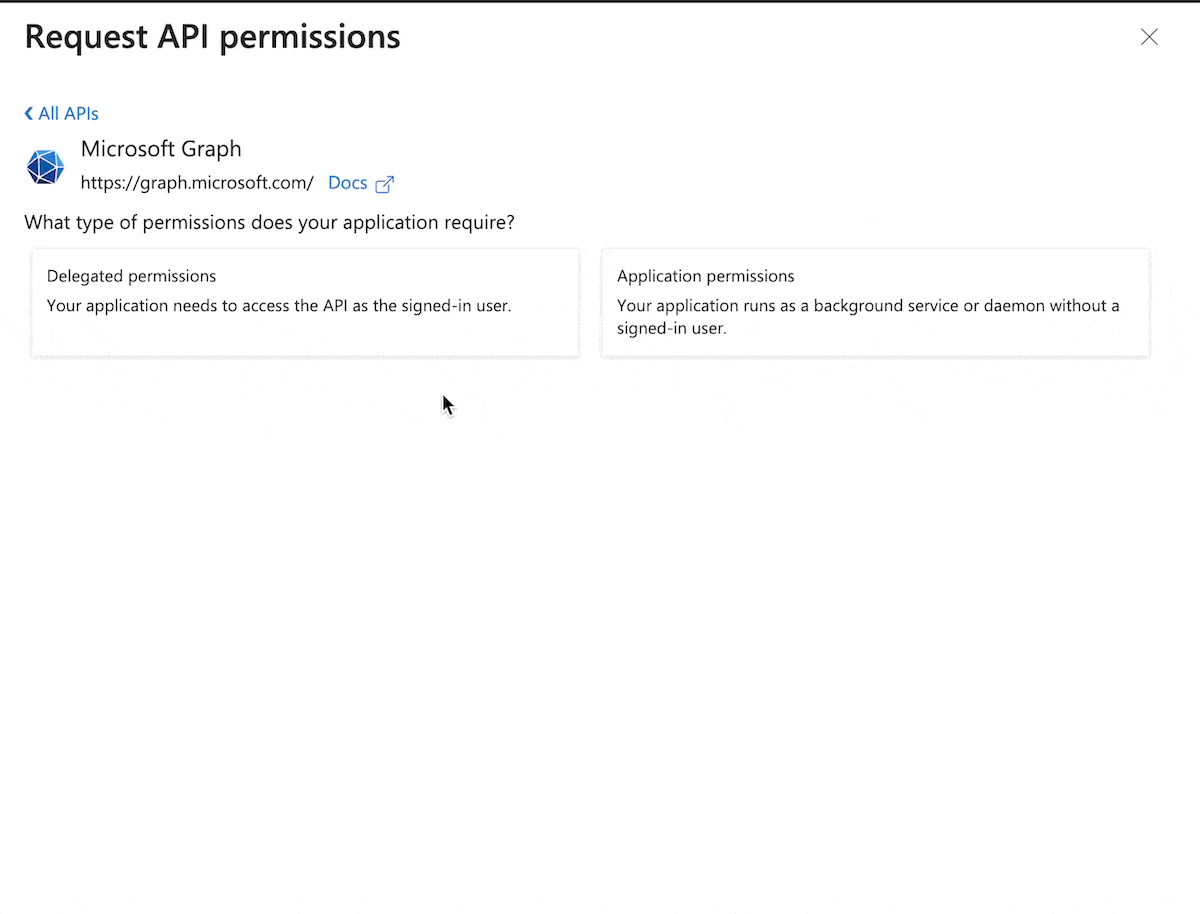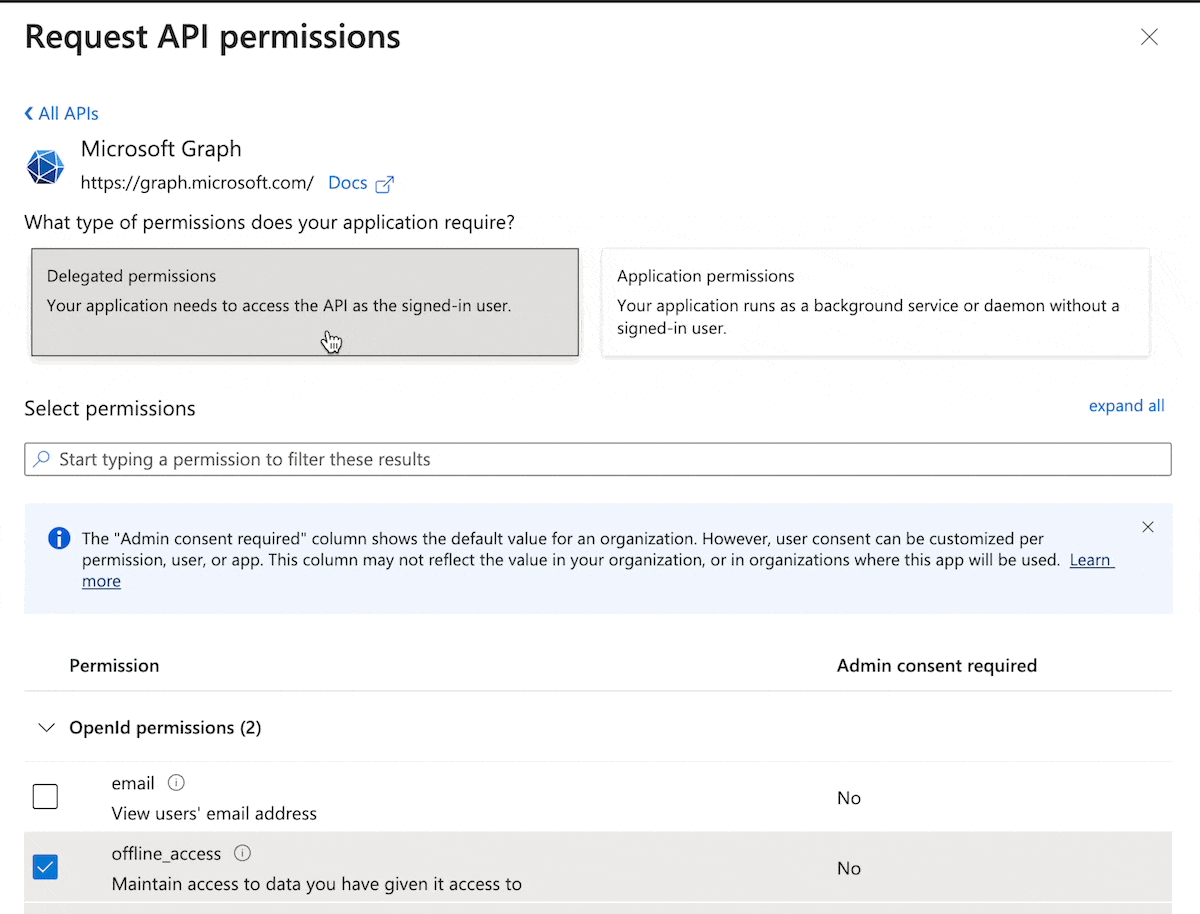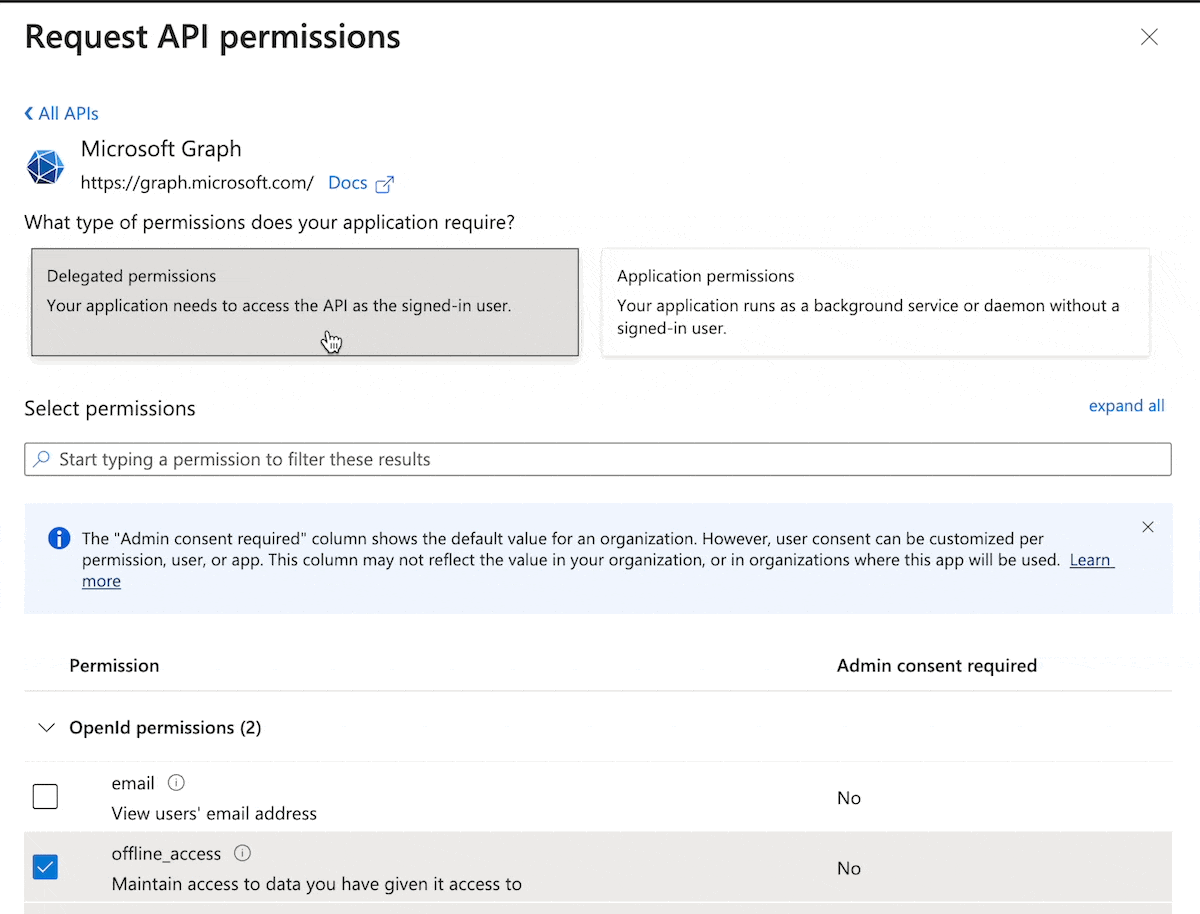
3. Add permissions
After your app is created, select API permissions in the sidebar.
Select Add a permission > Microsoft Graph > Delegated Permissions
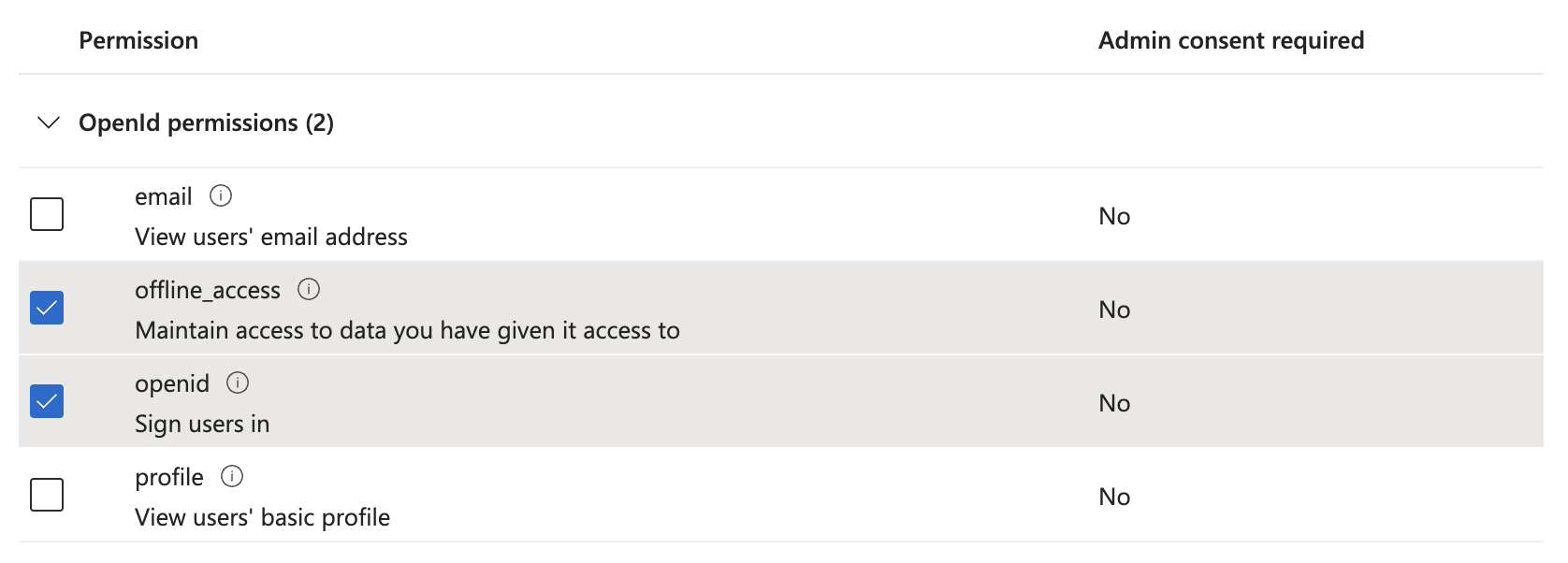
You can use the search option to search the following permissions:
openidoffline_accessUser.Read.AllUser.ReadBasic.All
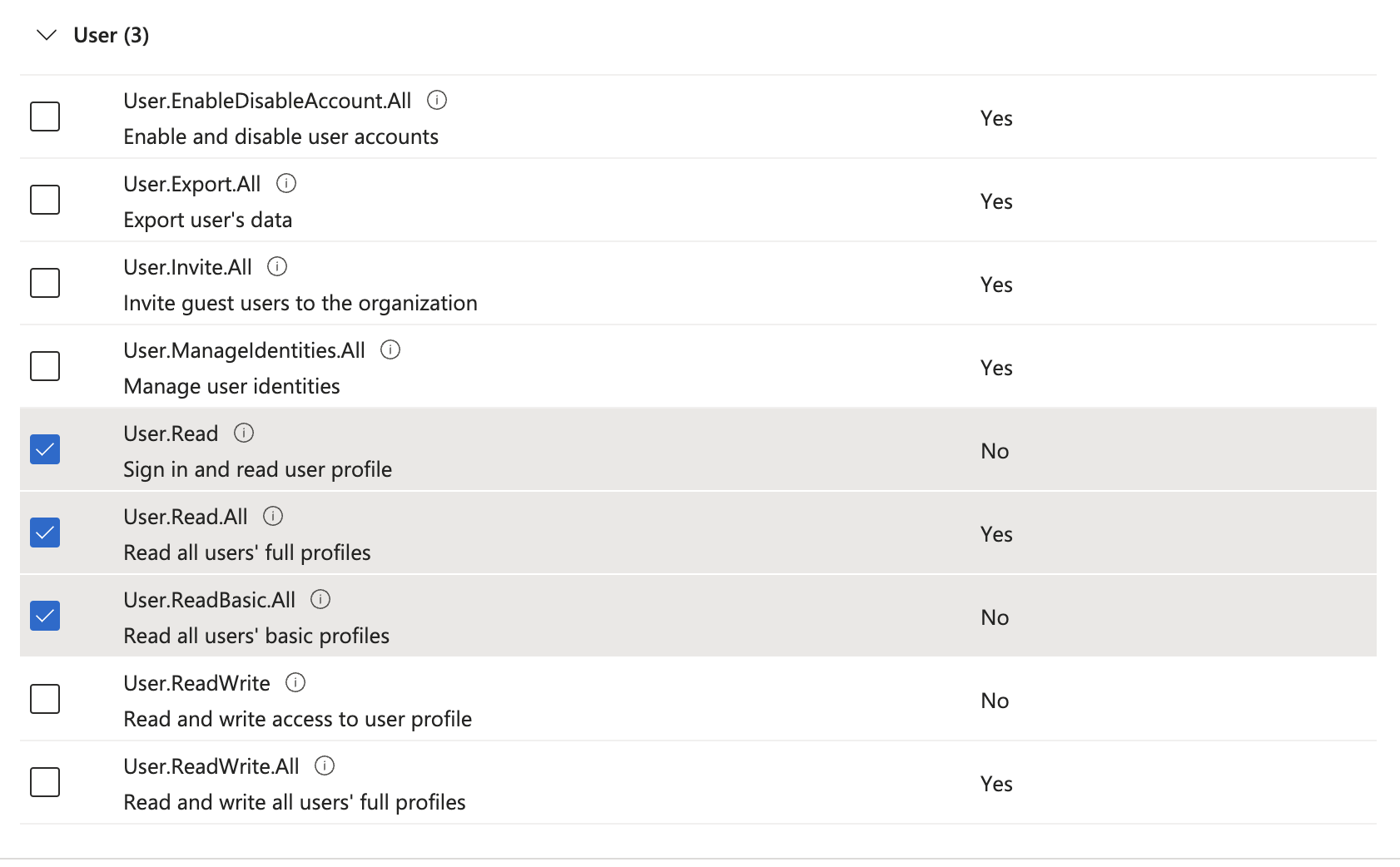
If your app only needs read access to employees, you can select User.Read.All & User.ReadBasic.All.
In case you want to create of modify employees, you can change the permissions to User.ReadWrite.All.
REMARK: Some permissions will require admin consent.
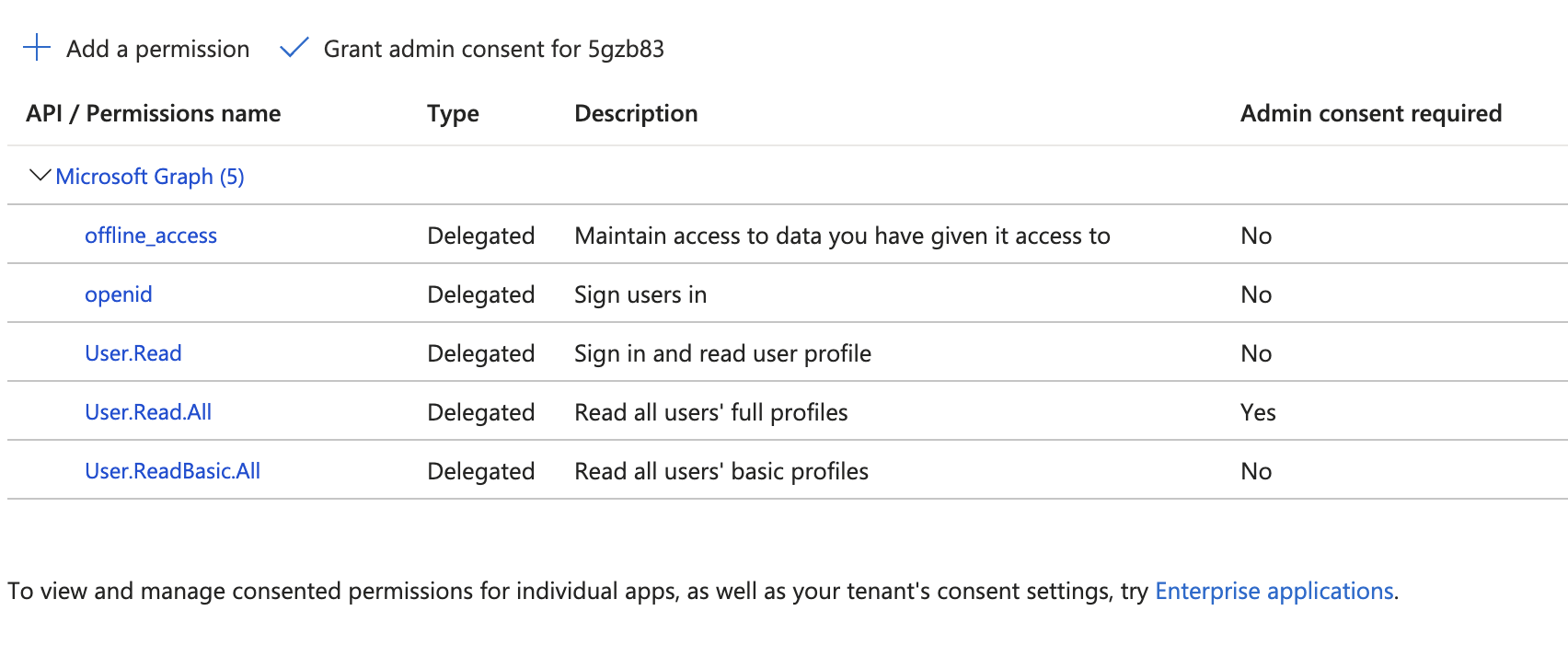
Resulting in a list of permissions with an approved status:
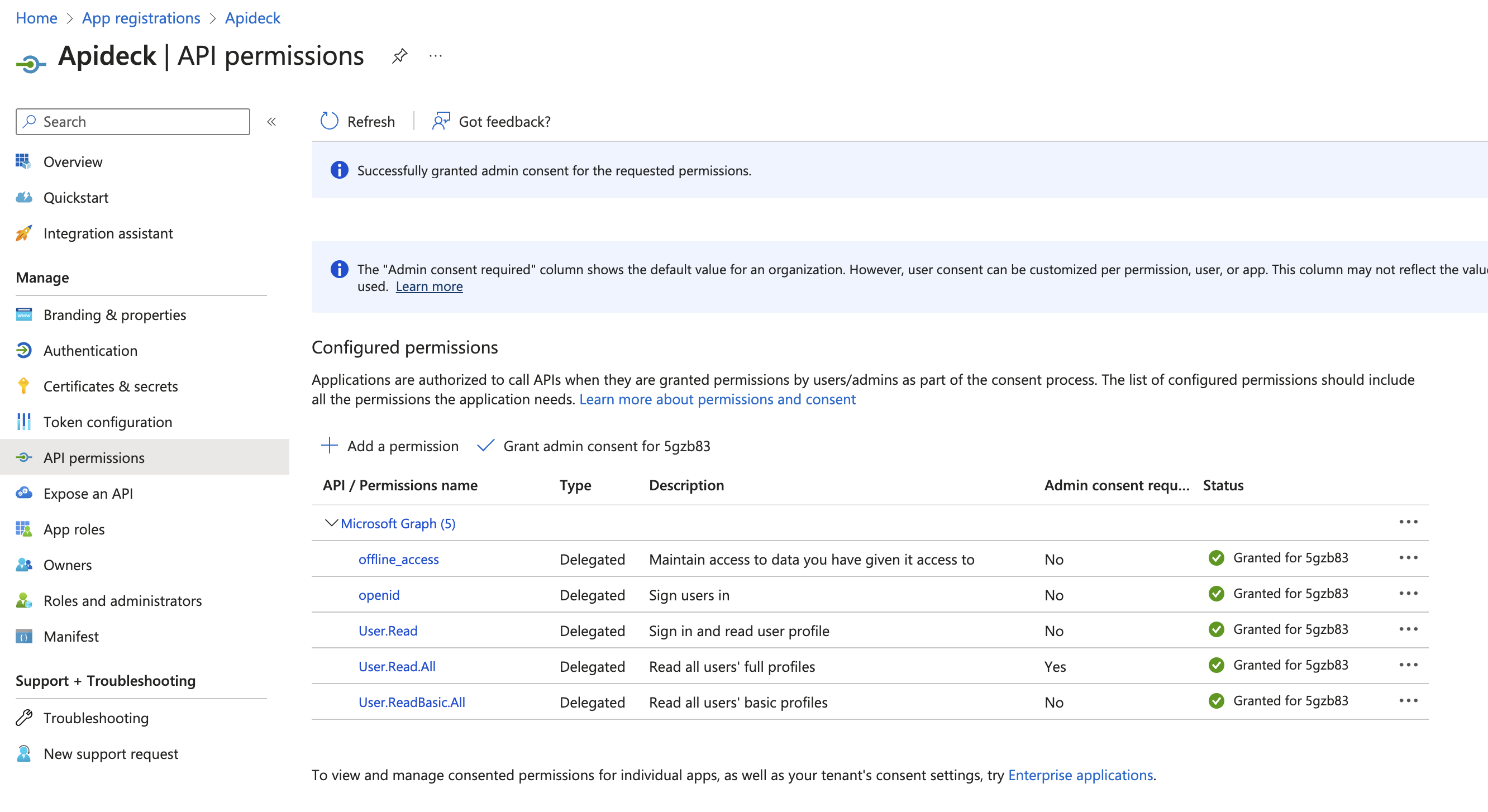
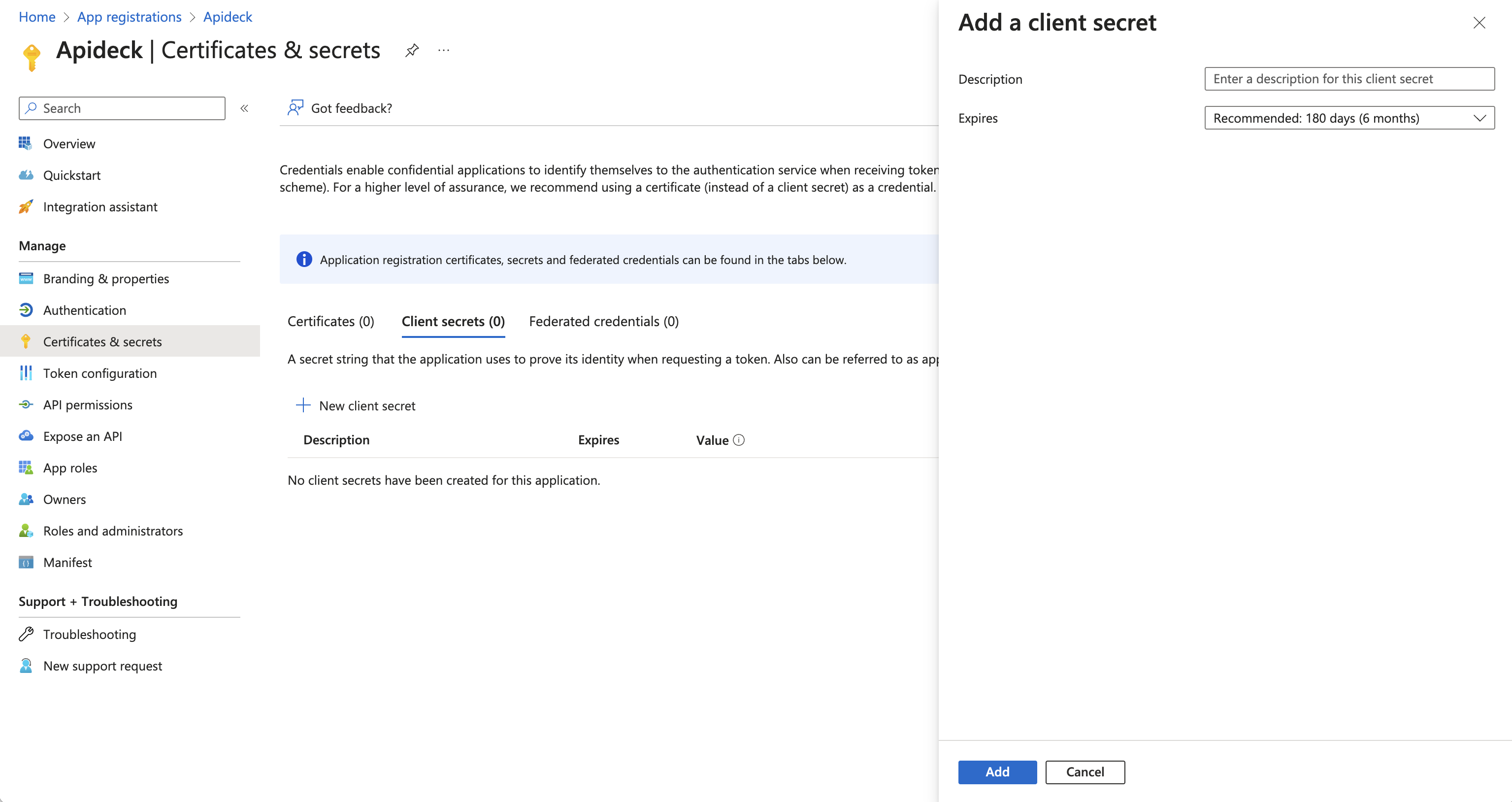
4. Generate credentials
Go to Certificates & secrets > Client secrets and select New client secret.
Enter a description and select an expiry time.
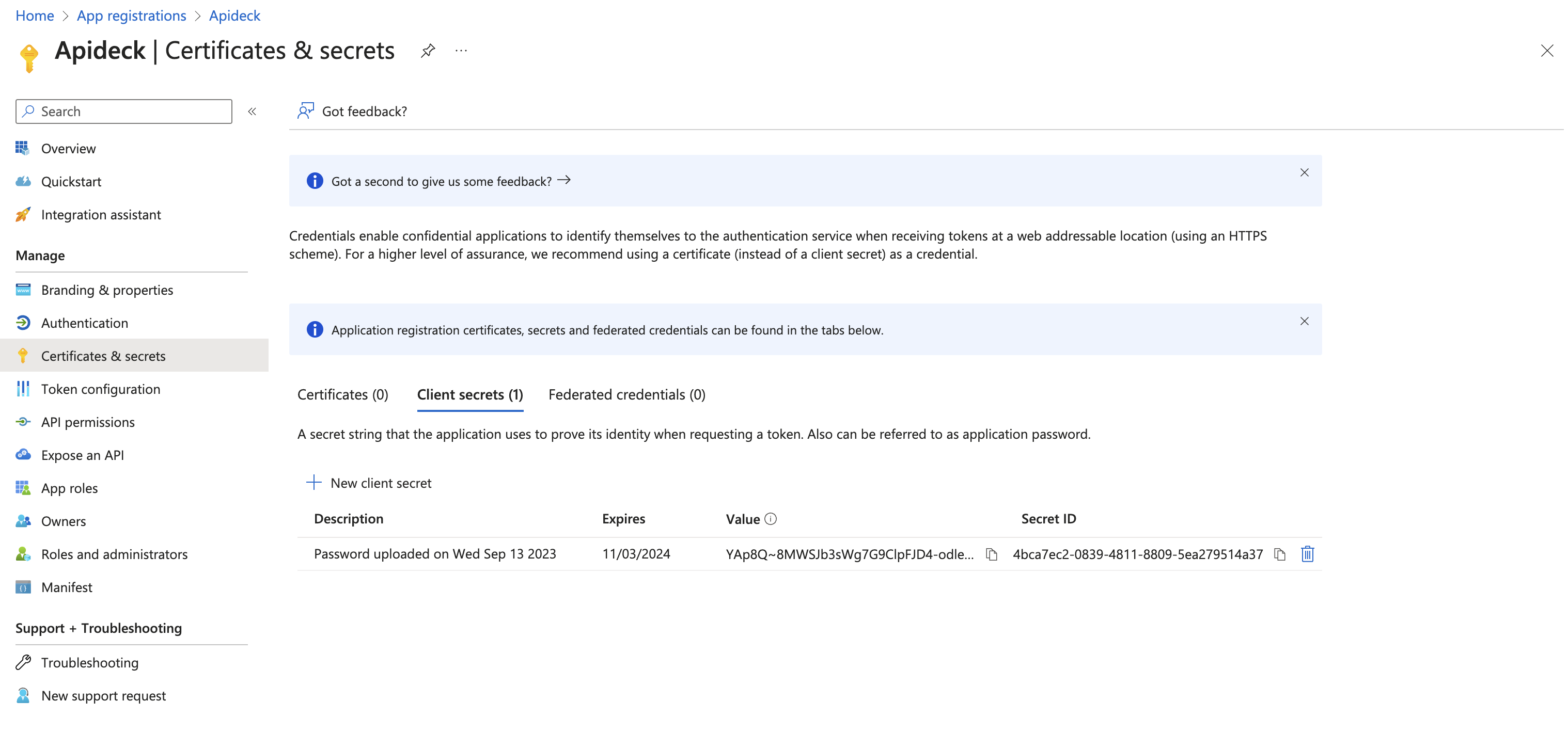
After the secret is generated, make note of the Value and Secret ID for later use. You will not be able to retrieve the value after leaving this page.
5. Configure in Apideck
Head over to the Apideck dashboard for Azure Active Directory
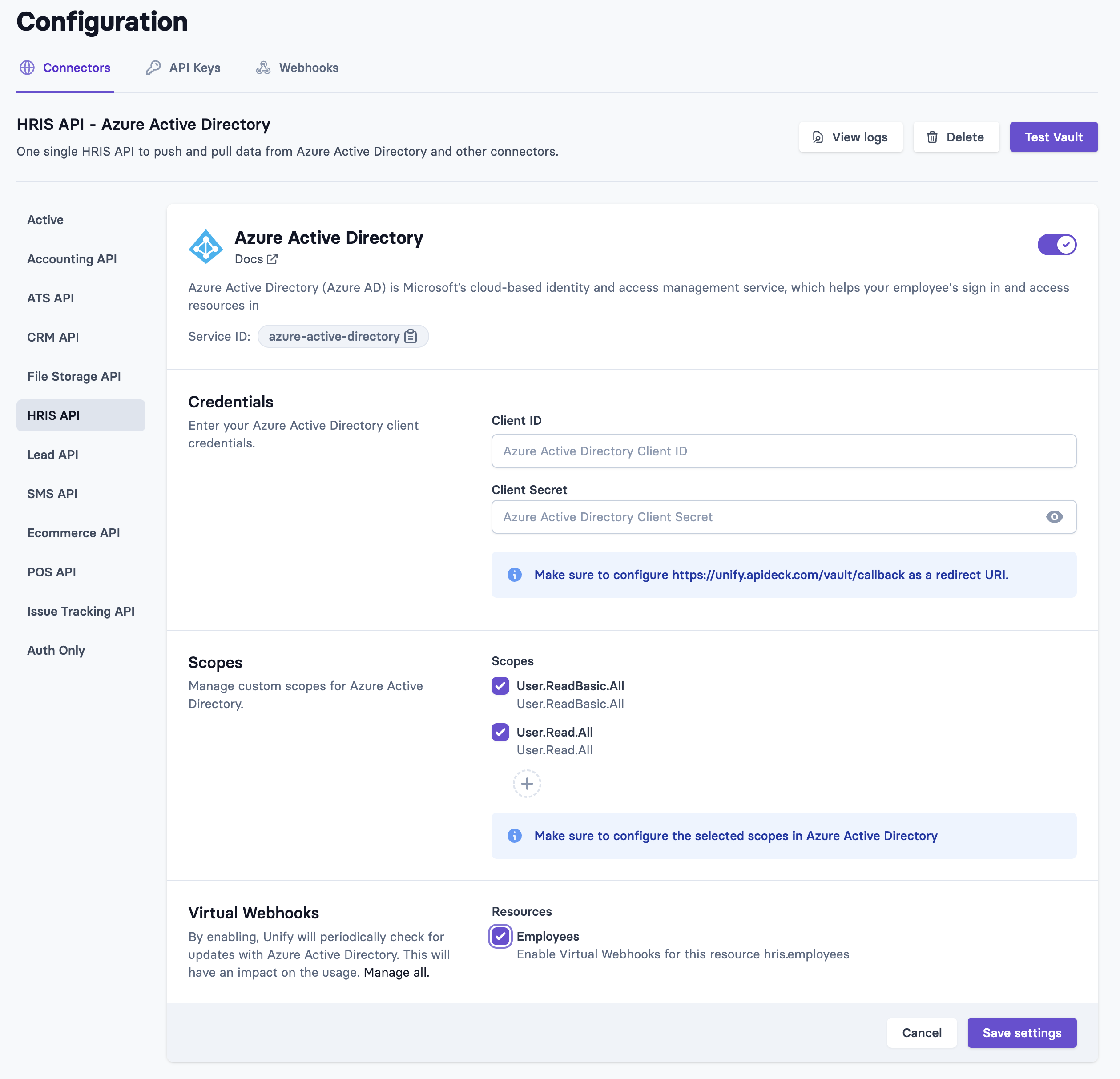
Enter the following credentials to setup the connection:
- Client ID: Application ID or the Secret ID of the client secret in Azure
- Client Secret: Value of the client secret in Azure NOTE: Don't use the
Secret IDhere
Note: double check that you copied the correct values from Step 4 since OneDrive calls the Client ID the Secret ID, which can confuse
Review the scopes to match them with the permissions that are granted with the Azure Application.
Once you've entered the credentials, click Save settings. You can now use the connection to retrieve data from Azure Active Directory.
6. Complete app metadata (optional)
Go back to your app in Azure and select Branding & properties. Complete the app with your company's icon, description and more.
More information
- https://learn.microsoft.com/en-us/onedrive/developer/rest-api/getting-started/app-registration
- https://learn.microsoft.com/en-us/graph/auth-register-app-v2
FAQ and troubleshooting
Error: OAuthCodeExchangeError
What causes the OAuthCodeExchangeError Azure Active Directory error?
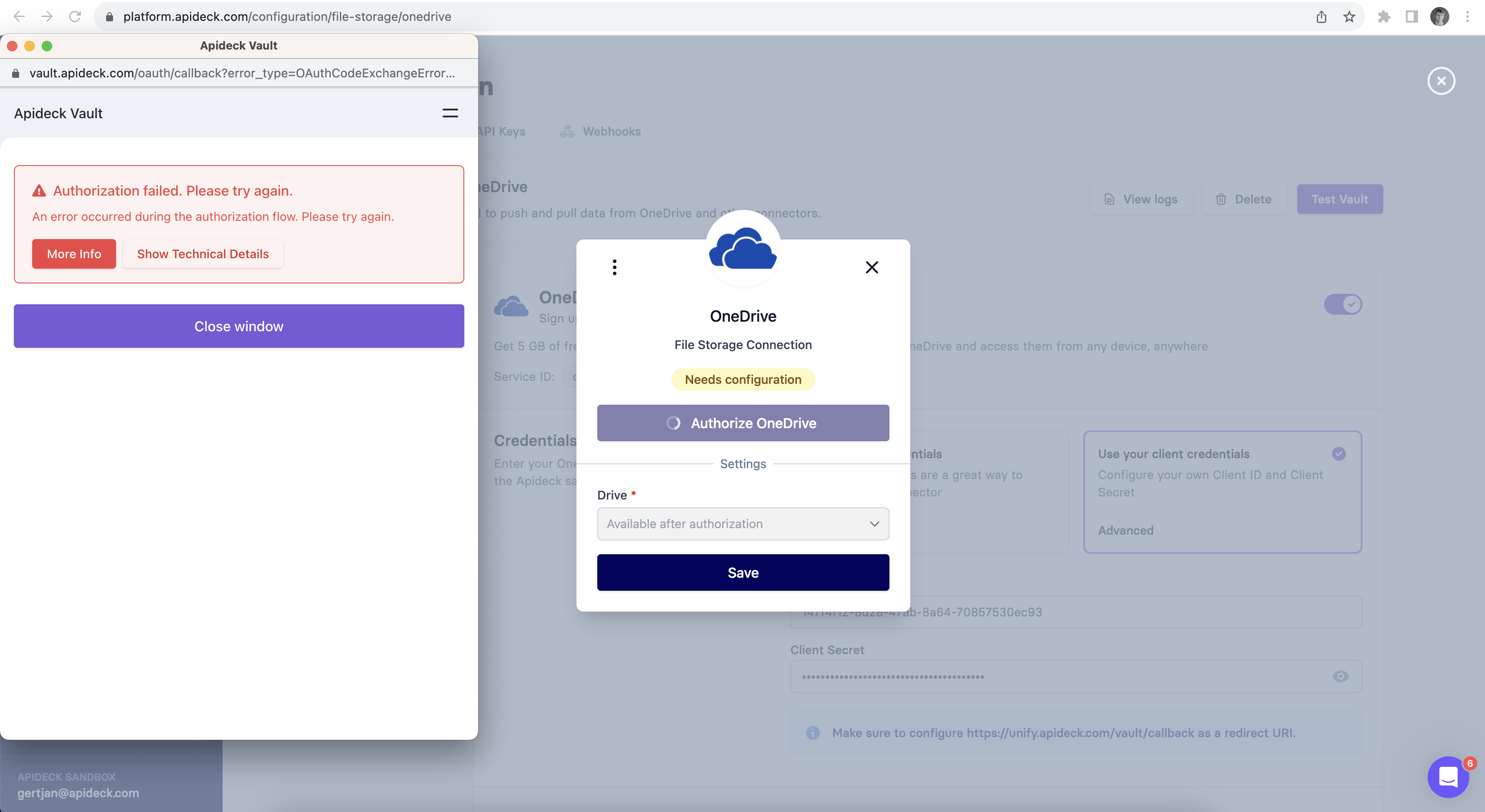
An OAuthCodeExchangeError happens when there is a mismatch of the custom credentials configured on the Azure Active Directory connector in Apideck.
It's a common error to copy the wrong settings to the Client ID and Client secret when setting up the Azure Active Directory connector for the first time. Double check that you copied the right values from Step 4. The Client Secret refers to the Value and not the Secret ID when creating the Client Secret